Crypto4A is Quantum-Safe Now Ask the right questions! The FIPS 140-3 Validation of a classic HSM does not make it quantum-safe A classic HSM providing PQC algorithm support does...
Just today NIST released its long-awaited report on the results of their Round 3 process for selecting post-quantum algorithms for standardization. The chosen algorithms CRYSTALS – Kyber, CRYSTALS- Dilithium,...
Recently, the Biden White House issued an Executive Order about the new visibilities and actions required by US government departments within a 6-month window, for an inventory of cryptography that is currently not...
In this blog, we will start to outline some thoughts on approaches for the current and coming crypto issues and how these will begin to impact our IT projects,...
This concern of “harvest now, decrypt later” has been around for many years and has been discussed by many experienced people from several perspectives – it is a real...
The NSA just released an FAQ addressing Quantum Computing and Post-Quantum Cryptography. This FAQ advises organizations that use public key cryptography as a business enabler and critical security component of their infrastructures. We...
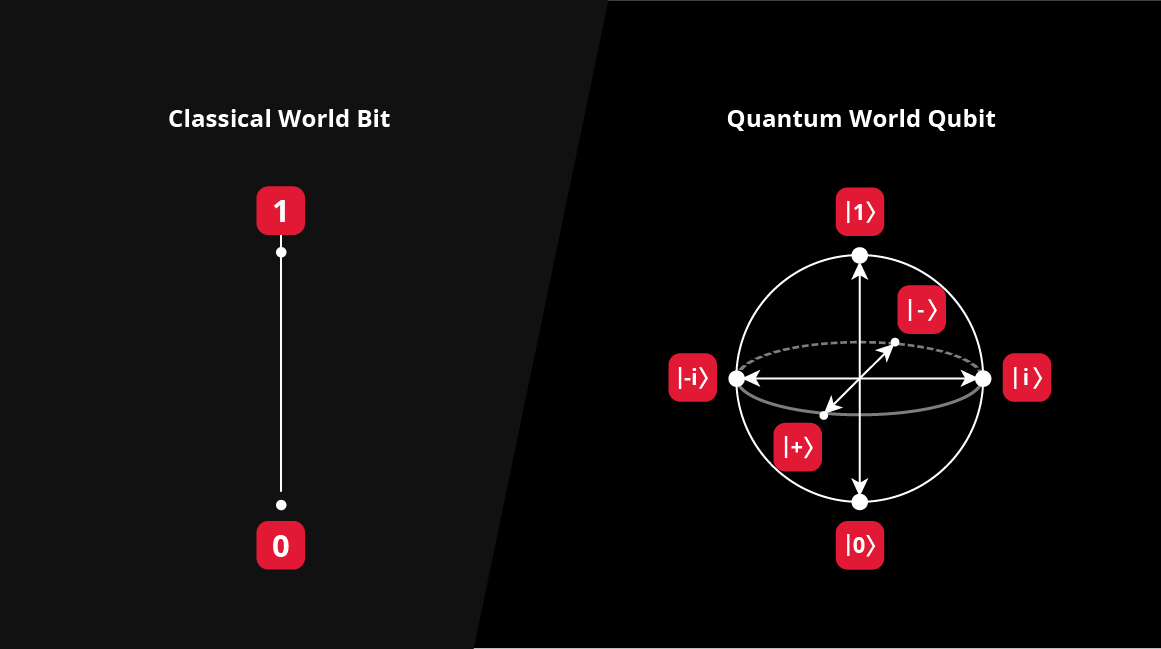
A quantum computer uses the properties of quantum mechanics to achieve incredible amounts of processing power. The Third State Makes the Difference For context, the classical computers we use...
Over the next 10 years some interesting challenges will be coming to the cyber security space. We are seeing nearly daily advancements in quantum computing, with the potential for...