This concern of “harvest now, decrypt later” has been around for many years and has been discussed by many experienced people from several perspectives – it is a real...
Where is your cryptography? Do you know where and how your crypto is currently being used in your organization and in your supply chain interactions. You will find it useful...
The NSA just released an FAQ addressing Quantum Computing and Post-Quantum Cryptography. This FAQ advises organizations that use public key cryptography as a business enabler and critical security component of their infrastructures. We...
The takeaways: digital trust underpins our entire digital economy, and makes digital transformation of businesses possible. With quantum computing on the horizon, however, a next generation of cryptography will...
“Any one who considers arithmetical methods of producing random digits is, of course, in a state of sin. For, as has been pointed out several times, there is no...
Digital trust is the confidence that we have that we can use digital systems safely, and it underpins our entire digital economy. The basis for digital trust is today’s...
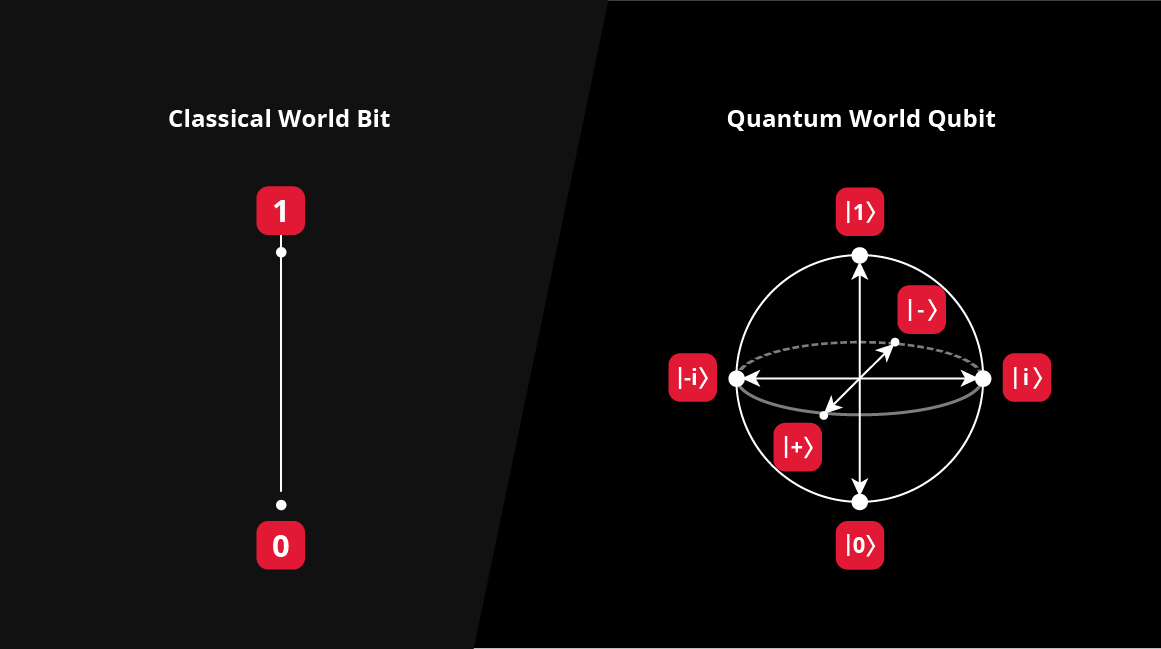
A quantum computer uses the properties of quantum mechanics to achieve incredible amounts of processing power. The Third State Makes the Difference For context, the classical computers we use...
Quantum computing is a serious threat to our current cryptographic standards. Hash-Based Signatures (HBS) are a quantum-safe option for firmware or code-signing applications. However, they have limitations in regards...
Over the next 10 years some interesting challenges will be coming to the cyber security space. We are seeing nearly daily advancements in quantum computing, with the potential for...